Lesson AI Summary
Introduction
Cyber security is a complex and ever evolving field which requires vigilant monitoring and detection of suspicious activities in order to protect data and systems from malicious actors. Suspicious activity detection is a critical element of cyber security and involves the identification of abnormal or suspicious behavior that may indicate a potential threat. This essay will discuss the importance of suspicious activity detection in cyber security, the methods used to detect suspicious activity, and the challenges associated with this process.
Body Paragraph 1
Suspicious activity detection is an important part of cyber security as it helps to identify and prevent potential threats before they can cause damage or disrupt operations. By monitoring the activities of users and applications, organizations can detect malicious activities such as malware, phishing, and other forms of cyber-attacks. This helps to protect the organization from financial losses, reputational damage, and the disruption of operations (Kumar, 2021).
Body Paragraph 2
There are various methods used to detect suspicious activity in cyber security, including the use of antivirus software, intrusion detection systems, and the analysis of system logs. Antivirus software scans for malicious files and programs that may have been introduced to the system, while intrusion detection systems detect abnormal user behavior and network traffic. System logs can be used to identify suspicious activities such as changes in user accounts, unauthorized access attempts, and other activities that may indicate a potential threat (Mizrahi, 2020).
Body Paragraph 3
Despite the various methods used to detect suspicious activities, there are still challenges associated with this process. Firstly, the sheer volume of data and logs can make it difficult to identify suspicious behavior. Additionally, malicious actors can use sophisticated methods to hide their activities, making them more difficult to detect. Furthermore, false positives can occur, resulting in false alarms and wasted resources (Garfinkel, 2021).
Conclusion
In conclusion, suspicious activity detection is a critical element of cyber security. Various methods such as antivirus software, intrusion detection systems, and system logs can be used to detect potential threats. However, there are still challenges associated with this process, such as the sheer volume of data and the possibility of false positives.
References
Garfinkel, S. (2021). The Challenges of Suspicious Activity Detection. Retrieved from https://www.schneier.com/blog/archives/2021/01/the_challenges.html
Kumar, A. (2021). 6 Benefits of Suspicious Activity Detection. Retrieved from https://www.forcepoint.com/blog/security-labs/6-benefits-suspicious-activity-detection
Mizrahi, R. (2020). Suspicious Activity Detection: What It Is and How To Implement It. Retrieved from https://www.cyberark.com/blog/suspicious-activity-detection-what-it-is-and-how-to-implement-it/
Objectives:
1. Students will be able to explain what suspicious activity detection is in terms of cybersecurity.
2. Students will be able to explain how suspicious activity detection works.
3. Students will be able to describe the methods used to maintain suspicious activity detection.
Materials:
- Computers/Laptops
- Internet Access
- Powerpoint Presentation
Time:
- 45 minutes
Procedure:
1. Introduction (5 minutes):
- Explain to the students what the lesson will be about and why it is important.
- Ask students to discuss what they already know about suspicious activity detection on cybersecurity.
2. Presentation (20 minutes):
- Provide students with a Powerpoint presentation covering the basics of suspicious activity detection, including the different methods used to detect and respond to suspicious activity.
3. Practice (20 minutes):
- Have students use their computers/laptops to research and practice how to detect and respond to suspicious activity.
4. Conclusion (5 minutes):
- Ask students to summarize what they have learned and discuss how they can use this knowledge in their professional lives.
Evaluation:
- Assign a short quiz at the end of the class to assess student understanding.
Course Title: Suspicious Activity Detection on Cybersecurity
Instructor:
Course Description: This course provides students with a comprehensive understanding of the various techniques and strategies used to detect suspicious activity on networks and computer systems. The course also covers topics such as malware analysis, network traffic analysis, and system log analysis.
Objectives:
• Understand the challenges and threats posed by malicious actors on the internet
• Develop an understanding of the different techniques and strategies used to detect suspicious activity
• Analyze malware to identify malicious code and behavior
• Analyze network traffic to detect malicious activity
• Analyze system logs to detect malicious activity
• Develop an understanding of the different tools used to detect suspicious activity
Course Content:
• Introduction to Cybersecurity
• Malware Analysis
• Network Traffic Analysis
• System Log Analysis
• Detection Tools and Techniques
• Case Studies
Assignments:
• Course discussion questions
• Reading assignments
• Lab assignments
• Quizzes
• Final project
Grading:
• Course discussion questions: 10%
• Reading assignments: 20%
• Lab assignments: 20%
• Quizzes: 20%
• Final project: 30%
Attendance/Participation:
Attendance and participation are expected of all students in this course. Attendance will be taken at the beginning of each class and the instructor reserves the right to lower a student’s grade if class attendance is unsatisfactory.
Classroom Etiquette:
• All students are expected to be prepared for class and actively participate in discussions.
• All students must be respectful of their classmates and the instructor.
• All students must abide by the University’s rules and regulations.
Academic Honesty:
All students are expected to adhere to the University’s policy on academic honesty. Any violation of this policy will result in disciplinary action.
References:
• Introduction to Information Security: A Strategic-Based Approach (2nd ed.), by Mark Ciampa
• The Basics of Cyber Safety, by Michael Gregg
• Cybersecurity Essentials, by Mark Ciampa
• Network Security: A Practical Approach, by William Stallings
1. Identify key characteristics of suspicious activity on a network and develop strategies for mitigating threats.
2. Utilize security tools and best practices to detect and investigate suspicious activity.
3. Interpret and analyze log data to identify potential signs of malicious activity.
4. Evaluate and select appropriate security controls and countermeasures for preventing and responding to suspicious activity.
5. Analyze network traffic for suspicious behavior and respond to incidents appropriately.
6. Develop and execute incident response plans for responding to suspected malicious activity.
7. Analyze network forensics evidence to identify suspicious activities and determine their source.
8. Develop an understanding of the legal and regulatory requirements related to suspicious activity detection and investigation.
1. What is the primary goal of suspicious activity detection?
a. To detect malicious activity
b. To prevent unauthorized access
c. To monitor user activity
d. To identify potential risks
Answer: a. To detect malicious activity
2. What type of suspicious activity can be detected by a cybersecurity system?
a. Unusual logins
b. Malware infections
c. Phishing attempts
d. All of the above
Answer: d. All of the above
3. What is the best way to detect suspicious activity?
a. Manual review of logs
b. Automated algorithms
c. Antivirus software
d. Firewall
Answer: b. Automated algorithms
4. What is the most important factor to consider when implementing suspicious activity detection?
a. Security policies
b. Threat intelligence
c. User authentication
d. Data privacy
Answer: b. Threat intelligence
5. What is the best way to respond to suspicious activity?
a. Ignore it
b. Block the user
c. Investigate the activity
d. Notify the user
Answer: c. Investigate the activity
AI Conversation
Lesson has no AI Conversation
Suspicious activity detection on Cybersecurity
machine learning algorithms
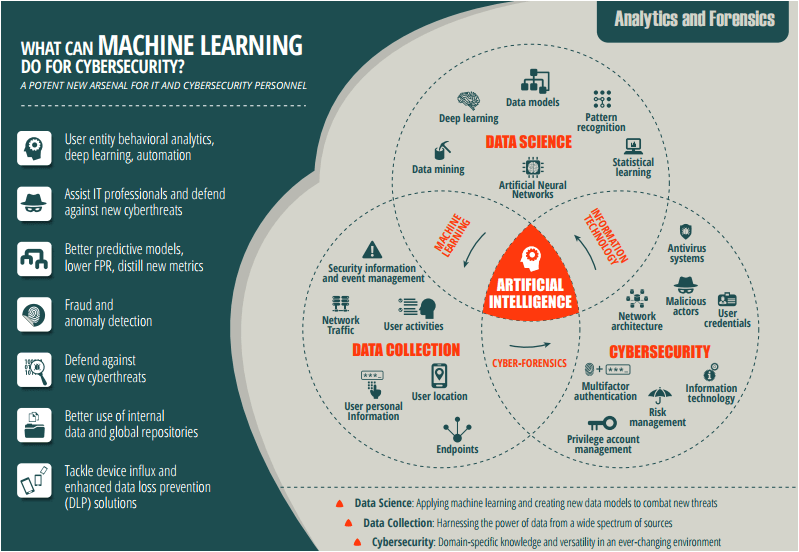
In the realm of cybersecurity, machine learning algorithms shine, Detecting suspicious activity, a task quite divine. They analyze patterns, anomalies they find, Protecting our data, leaving no vulnerabilities behind.
https://www.youtube.com/watch?v=OBK7MtqXj3Q
threat intelligence

In the realm of cybersecurity, threat intelligence shines, Detecting suspicious activity, it intertwines. With knowledge and insight, it unveils the unknown, Protecting systems, like a guardian, it's shown. A vigilant ally, in the fight against cybercrime, Threat intelligence, a poetic paradigm.
https://www.youtube.com/watch?v=VNp35Uw_bSM
endpoint detection and response (edr)
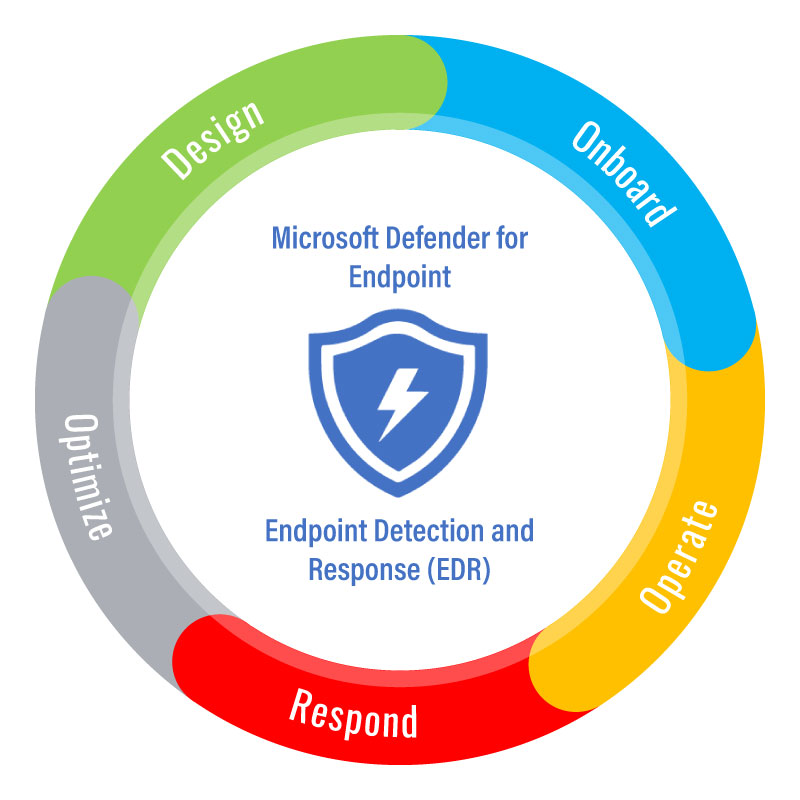
In the realm of cybersecurity, EDR shines, Detecting suspicious activity, it defines. Endpoint Detection and Response, its name, Keeps threats at bay, a vigilant flame. With its watchful eye, it safeguards our cyber domain.
https://www.youtube.com/watch?v=55GaIolVVqI
behavioral analysis

In the realm of cybersecurity's vigilant eye, Behavioral analysis detects suspicious activity, oh my! Through patterns and anomalies, it seeks to find, Cyber threats lurking, with a watchful mind. With just 50 words, a summary so concise, Unveiling dangers, protecting us with cyber-sleight.
https://www.youtube.com/watch?v=KqwOAGxus6I
anomaly detection
In the realm of cybersecurity's vigilant gaze, Anomaly detection sets ablaze. Seeking out suspicious activity's trace, Unveiling threats lurking in cyberspace. With algorithms keen, it swiftly detects, Protecting systems from cyber intruders' effects.

https://www.youtube.com/watch?v=wzRPzfKJYyU
log analysis

In the realm of cybersecurity's vigilant eye, Log analysis unveils the secrets that lie. Suspicious activity, it seeks to detect, Through logs, it uncovers the threats we suspect. With keen observation, it unravels the plot, Protecting our digital realm, it hits the spot.
https://www.youtube.com/watch?v=-T6oue5E4KQ
network traffic analysis
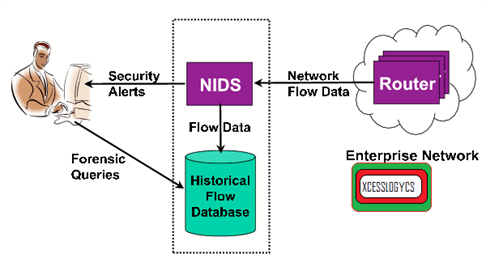
https://www.youtube.com/watch?v=o-QNMSPbOGY
In the realm of cybersecurity, network traffic analysis unveils secrets untold. It unravels the dance of data, exposing suspicious activity bold. With keen eyes, it detects the signs, revealing threats that lurk in the shadows. A poetic symphony of bytes, protecting the digital meadows.
intrusion detection

https://www.youtube.com/watch?v=iBsGSsbDMyw
In the realm of cyber defense, intrusion detection unveils, A vigilant eye, it casts, on suspicious activity's trails. Within the digital realm, it seeks to uncover, The hidden threats that lurk, to protect and discover. A guardian of cybersecurity, it stands tall, Detecting intrusions, safeguarding one and all.
user entity behavior analytics (ueba)

In the realm of cybersecurity, User Entity Behavior Analytics (UEBA) shines, Detecting suspicious activity, it intertwines, Analyzing user behavior with finesse, Identifying threats, no matter how complex, A powerful tool to keep cyber threats confined.
https://www.youtube.com/watch?v=j29XwVsMW-s
security information and event management (siem)
https://www.youtube.com/watch?v=IeN-wjHetfA
In the realm of cyber defense, SIEM stands tall, Detecting suspicious activity, it answers the call. Gathering data, analyzing with precision, Protecting systems from cyber intrusion. With vigilance and insight, it keeps threats at bay, Securing our digital world, day by day.